When the Clock Starts Ticking
Assessing Materiality of Cybersecurity Incidents
Contents
The landscape of cybersecurity incidents has evolved rapidly, marked by an increase in both frequency and sophistication. This uptick is paralleled by a significant shift in regulatory expectations, and enhanced disclosure requirements.
Introduction
As we navigate through the surge of cybersecurity incidents, it's crucial for us to rapidly analyze and interpret the extensive volume of intricate data—ranging from scrutinizing logs to discern user actions, to examining packets and netflow for detecting lateral movement. This capability is not simply beneficial; it is essential for our operational integrity and resilience.
The complexity and pervasiveness of cyber threats today make the need for rapid and accurate materiality assessment of incidents indispensable. Organizations are compelled to disclose breaches promptly; by doing so early, they can significantly curtail the ramifications.
Swift disclosure not only aligns with compliance mandates but also serves as a critical strategy to limit adverse impacts. It is essential in upholding stakeholder confidence and ensuring favorable standing with regulatory bodies.
Assessing the materiality of cybersecurity incidents
When determining the materiality of cybersecurity incidents, companies are obligated to follow the guidelines established by the Securities and Exchange Commission (SEC) in the US, the Financial Conduct Authority (FCA) in the UK, and the European Securities and Markets Authority (ESMA) in the European Union, with each region's regulations stressing the importance of accurately assessing the significance of the incident.
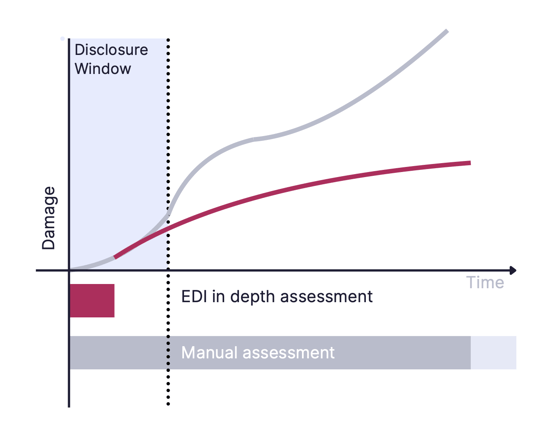
In evaluating the materiality of a cyber incident, it is crucial to acknowledge that the wider the gap between the initial exposure and the subsequent disclosure, the greater the potential for damage.
Key factors to consider include:
- Potential damage to the company's reputation.
- Disruption to business operations.
- Impact from supply chain exposures
- Effects on competitive position.
- Risk of litigation or regulatory actions by both domestic and international authorities.
- Changes to the business's overall value.
- Both the immediate and longer-term financial costs associated with the incident.
It swiftly becomes evident that a comprehensive grasp of the compromised data, encompassing files, logs, credentials, among other types, is pivotal for impacting the majority of the previously mentioned considerations.
The capability of looking within those files to assess their importance is what makes the biggest time difference.
And, time is key before any sensitive information can be compiled and weaponized by bad actors and have exponential consequences on the company’s operations, reputation and most importantly value.
Timeline of Actions After a Cybersecurity Incident
Organizations must establish a systematic approach for evaluating cyber incidents. This process begins with the collection and analysis of information by security and IT teams, followed by escalation to relevant departments such as finance and legal.
-
Immediate Identification and Documentation
-
Assessment and Containment
-
Notification of Internal Teams
-
Materiality Assessment
Conduct a materiality assessment considering both quantitative and qualitative factors, such as potential harm to reputation, operational disruption, legal implications, and financial impacts.
-
Engagement with External Experts
-
Regulatory Compliance Checks
-
Stakeholder Communication
-
Remediation and Recovery
-
Post-Incident Review
-
Disclosure
This timeline can be significantly accelerated through instant, complete and actionable intelligence about the entirety of your data.
This is where EDI - Exposed Data Intelligence can make a significant difference.
Exposed Data Intelligence (EDI)
EDI is a new category introducing AI assisted, sophisticated data analysis, actively seeking out exposed data risks before they cause harm.
Exposed Data Intelligence gives regulated institutions actionable intelligence faster than ever before for mitigating the risks and consequences of data exposures.
This approach transcends traditional limitations of merely identifying document names and types, employing AI to delve into the depths of the contents within those documents and files.
By analysing specifics such as the type of entity affected, who is impacted and how, as well as the nature of the information contained, EDI marks a significant leap in comprehending the full scope of an incident.
All of these advancements are achieved without the need for extensive analyst teams, thereby reducing the potential for human error.
Expedited materiality assessments with the help of EDI
Unlike traditional methodologies that focus primarily on identifying how a breach occurred and who is behind it, our approach centers on a detailed assessment of the specific data that was compromised.
This precision enables a swift, thorough evaluation of the risk associated with the accessed data, not only helping you stay within legally mandated disclosure windows but, more importantly, significantly decreasing the financial and reputational damage.
Furthermore, a granular view of the contents of Exposed Data Entities extends to enhancing documentation and improves regulatory compliance checks as well as the quality of stakeholder reporting and communication.
The Lab 1 EDI Platform
The Lab 1 EDI Platform is revolutionizing how businesses handle data exposure by offering an automated, efficient, and intelligent solution.
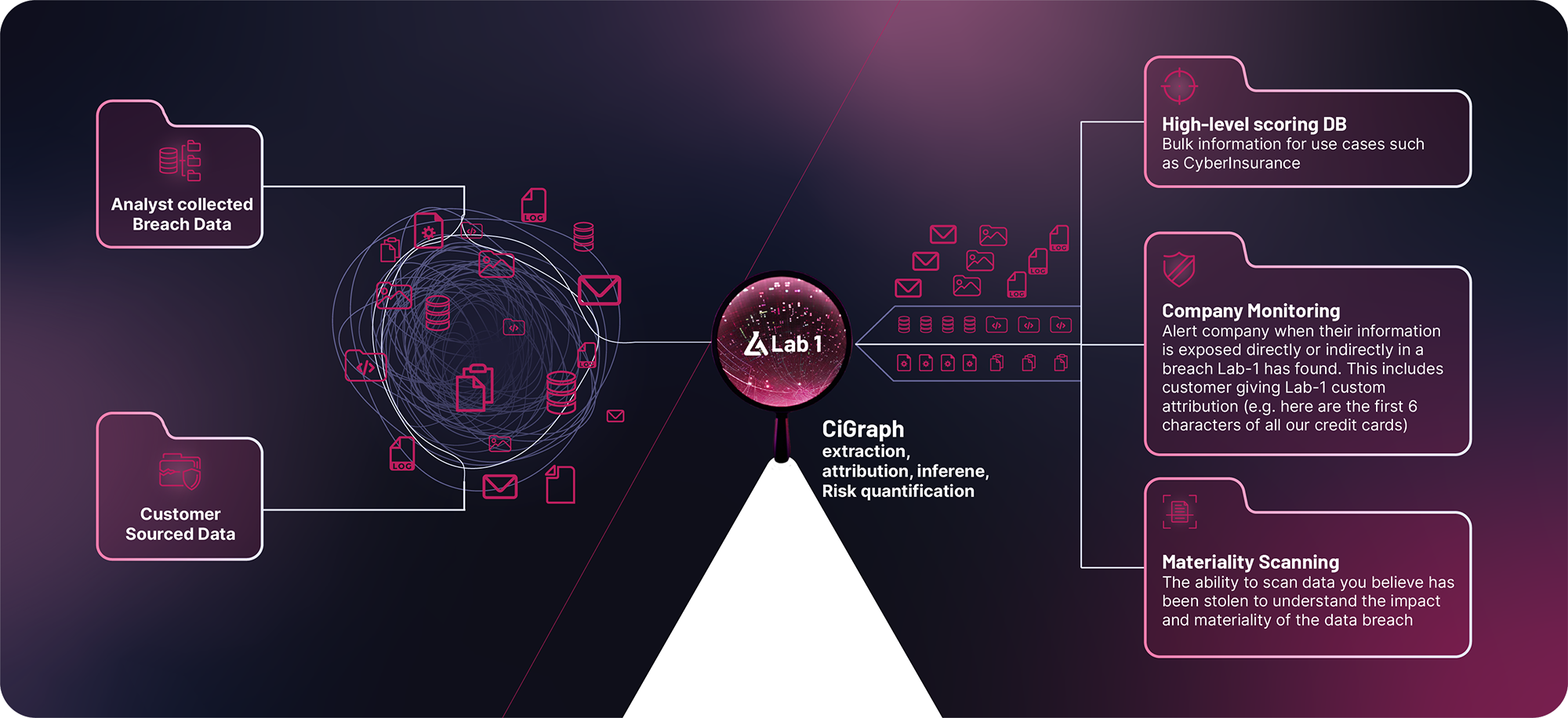
Our platform continuously monitors for exposed data. We providing you with high fidelity intelligence and alerts, allowing you know if you are at risk.
SHARE