Forcing Balance in Exposed Data Management
Our Gen AI Agents continuously monitor exposed data. We provide you with high fidelity intelligence and alerts, allowing you know both IF and HOW you are at risk and helping you close the loop faster.
We look everywhere, for all data, all of the time
quicker analysis
entities added
every second
data entities
under management
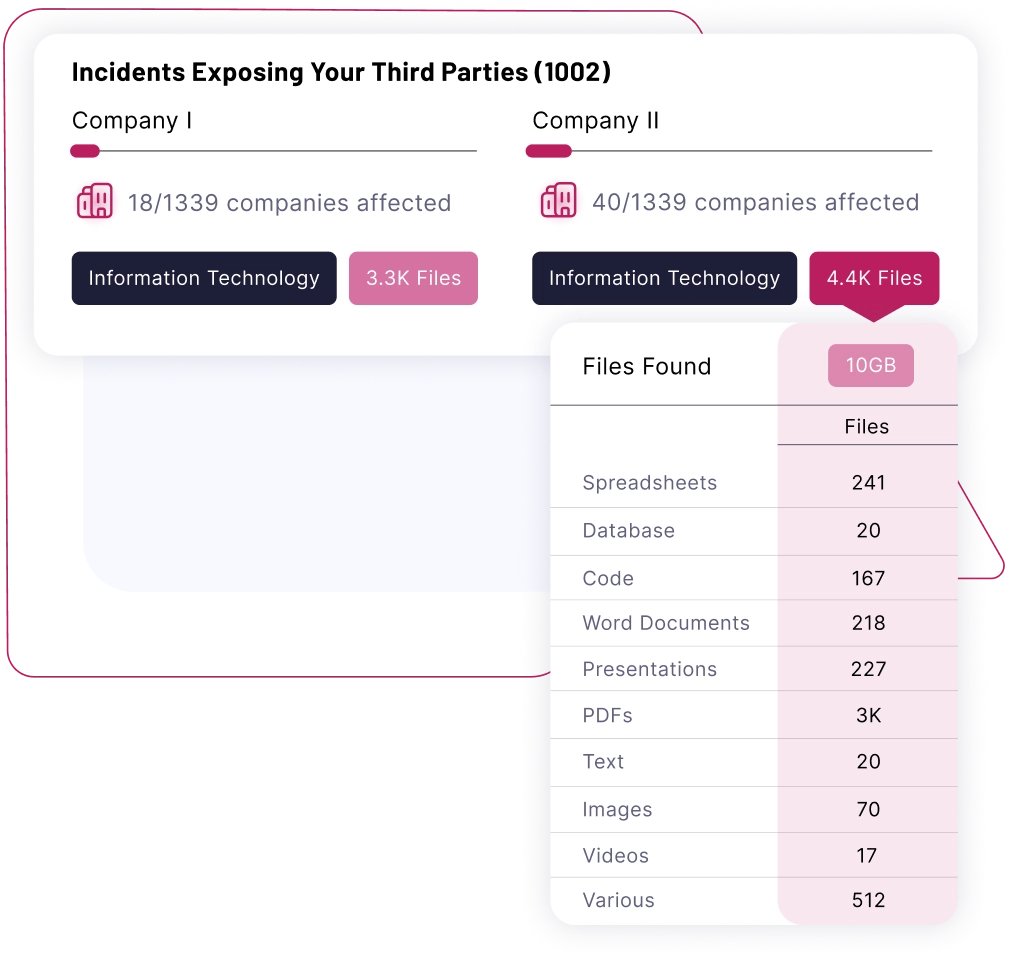
Every Incident Monitored
It all starts with monitoring and capturing incident data. We have now captured over 30TB of data extracting 10s millions of files from thousands of incidents.
All Data Entities Extracted
We extracted tens of billions of Exposed Data Entities (EDEs), compromising billions of identities and millions of organisations. And continue to extract over 629 entities per second.
.webp)
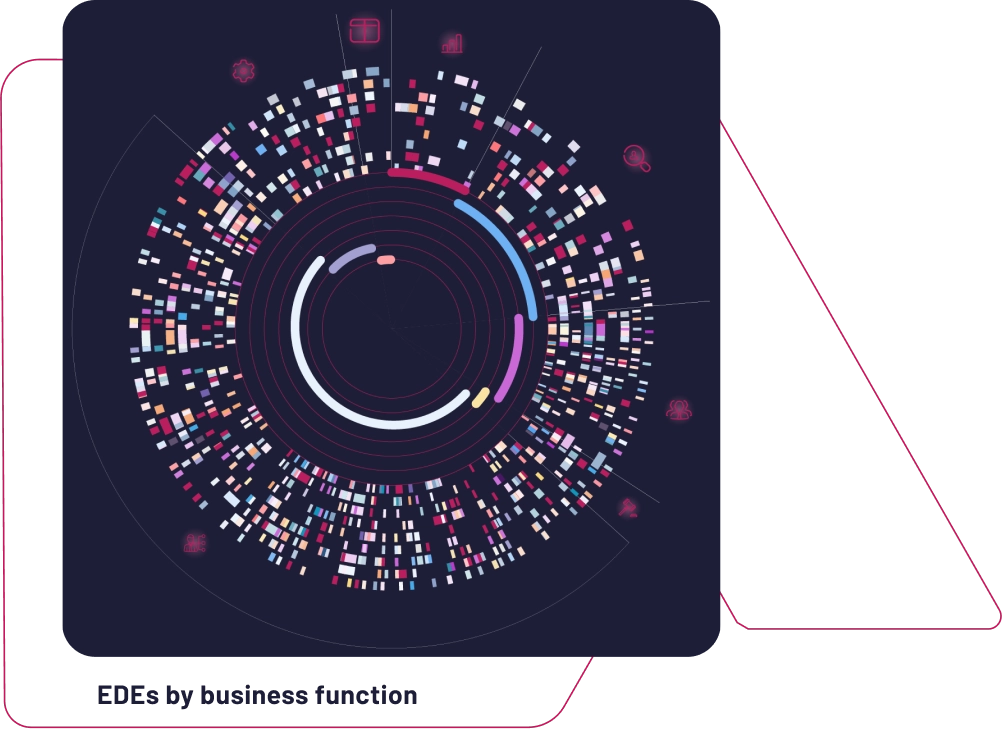
All Dots Connected
We use our sophisticated approach to understand the breadth, depth and dependencies of exposed data. Looking not only at which organizations and third parties have been exposed but also the content of the exposed files, we help you quantify potential risks.
How it works
Our most advanced approach for exposed data intelligence:
Discovery at Depth:
Our platform scrutinises the clear, dark and deep web as well as various messaging applications to identify direct and indirect data exposures.
Speed at Scale:
Through our mix of data sources and AI data processing, we can analyse vast volumes of breached data quicker than any other known system or service.
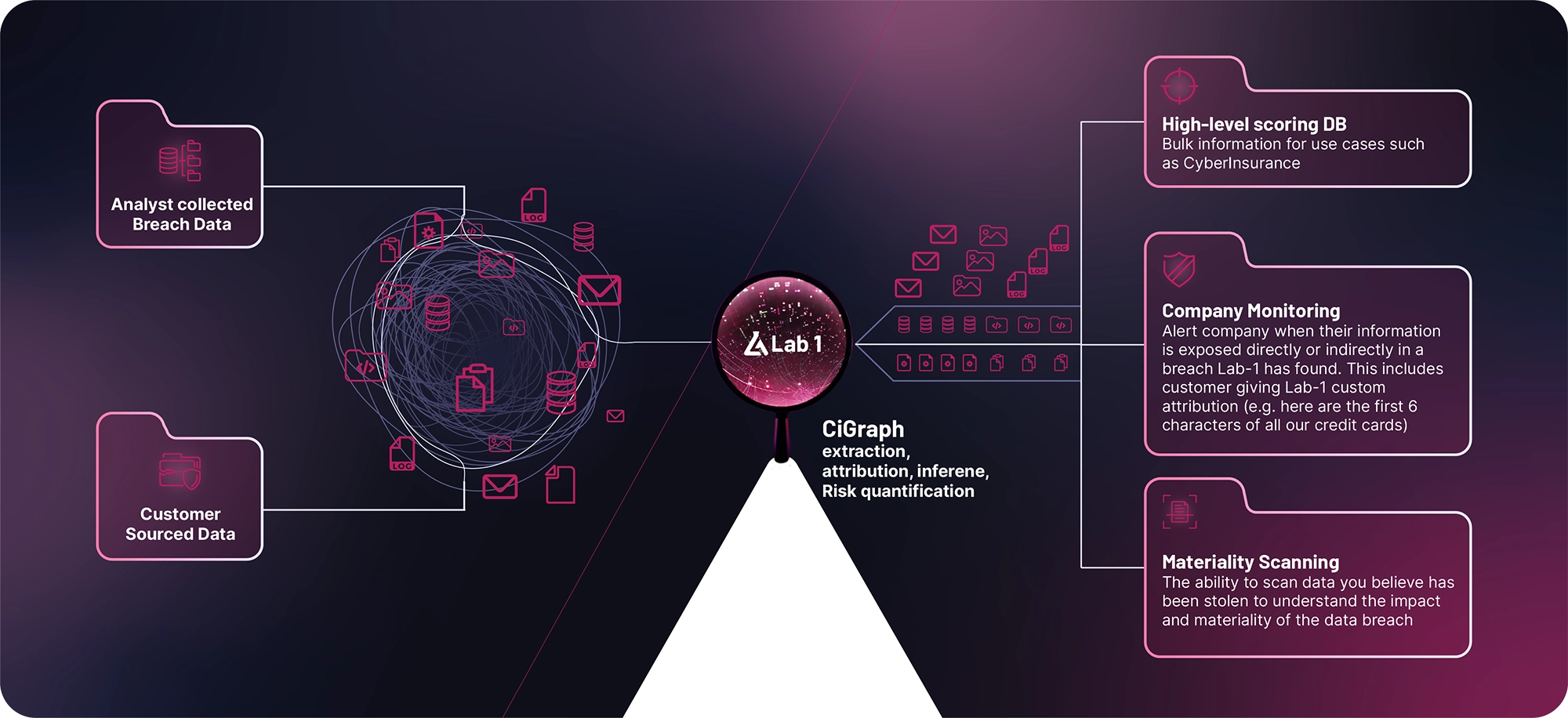
Core Components
Company Scoring
Businesses can obtain a risk score based on exposed data, which is critical for self-assessment, supply chain evaluation, cyber insurers, and Attack Surface Management providers.
Company Monitoring
Our platform seamlessly integrates with existing threat-monitoring processes, alerting companies and managed service partners to any data exposures.
Data Scanning
Offering high-fidelity intelligence, the platform aids security or incident response teams in the effective remediation of suspected data exposures
Ready to Get Started?
Gain Visibility into the World's Exposed Data