Anatomy of a Breach Report
A breach isn't just a leak. It's a weapon, repurposed again and again.
Contents
Cyberattacks and fraud are growing in sophistication and intent, targeting the very structure of our organizations. To achieve this, threat actors are studying us, probing every corner of our business, from third-party vendors to forgotten cloud and IT assets, to find our weakest points to exploit.
With cybercriminals now behaving like data scientists to unearth these valuable insights to fuel cyberattacks and fraud, unstructured data cannot be ignored. Internal documents, credentials, and supplier communications all can be pieced together to paint a detailed picture of how we operate.
That’s why accurately assessing the impact of a breach now means uncovering not just if data was leaked, but what was leaked, how it can be used, and who might be affected.
The real cost of a breach isn’t just felt in the immediate aftermath; it’s in the time spent unaware of what’s been exposed and the unknown risks to your organization. Without visibility into your exposure, organizations risk increasing consequences before they even begin to respond to threats.
Analyzing 141 million files across 1,297 data breaches, The Anatomy of a Breach is the biggest ever content-level analysis of breached datasets, exposing the monumental risk that unstructured data poses to organizations, their employees, and customers.
Breach Weaponization, by the Numbers.
According to the report:
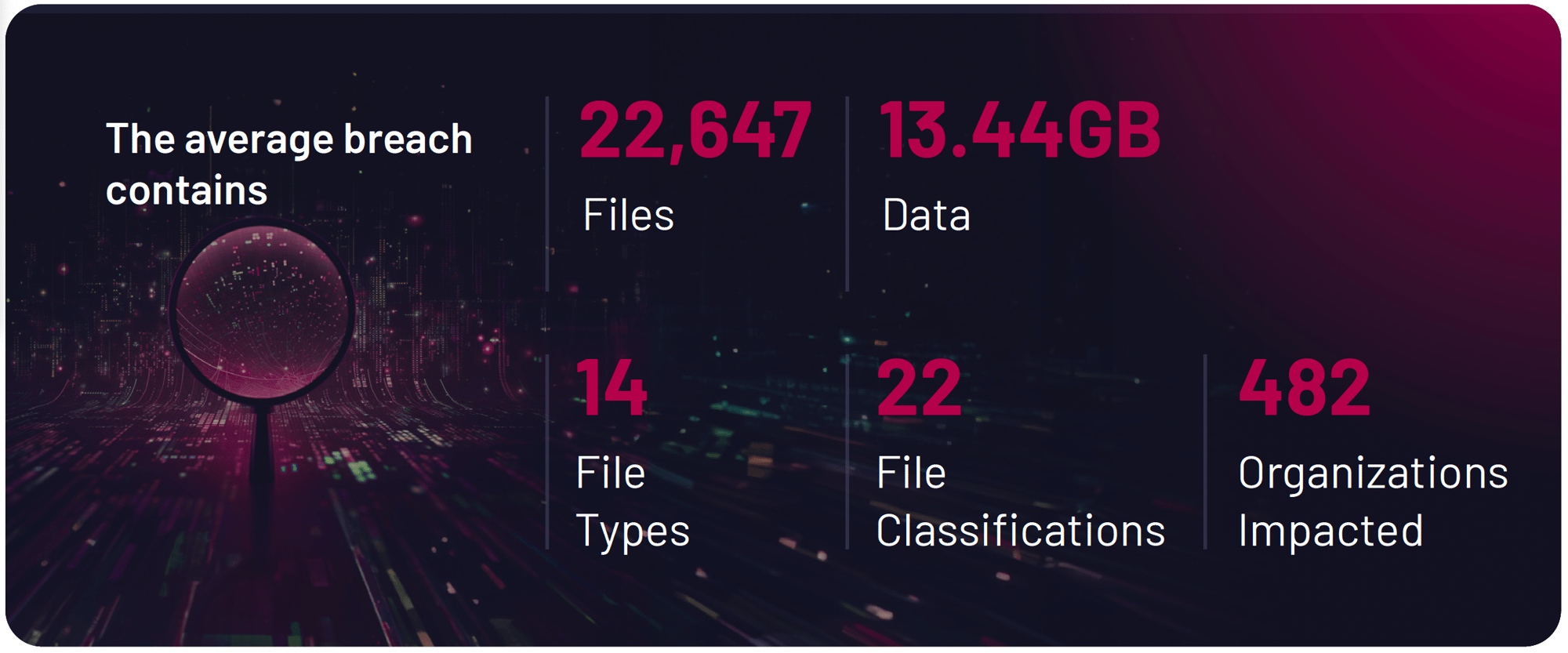
- 93% of incidents contain financial data
- U.S. Social Security Numbers were identified in half of all incidents analyzed
- 54 email addresses are exposed per file.
- 36% leaked IBANs
Your next breach might already be in motion.
What You'll Learn
- How prevalent sensitive commercial and personal information is in unstructured data, including HR records, contracts, bank statements, and Social Security Numbers
- How this exposed data is being used as a weapon to fuel downstream cyberattacks and fraud
- What the composition of a “typical” breach looks like in 2025
- How to take a content-aware approach to breach analysis that goes beyond incident counts
Understand the real anatomy of a breach.

SHARE