AI Data Intelligence Across Open, Dark, and Private Sources.
From breach detection to enterprise oversight, Lab 1's AI inspects every file, discovering what’s at risk, in hours instead of weeks and months.
Report The Anatomy of a Breach
Not all breach data is equal.
Download our analysis of 141M files across 1,297 breaches.
How Lab 1's AI Data Intelligence Application works
Designed for anyone looking to proactively discover, detect risk, and prevent loss across internal, structured and unstructured data.
.png?width=2000&height=1031&name=How%20Data%20Intelligence%20works%20%20v02%20(1).png)
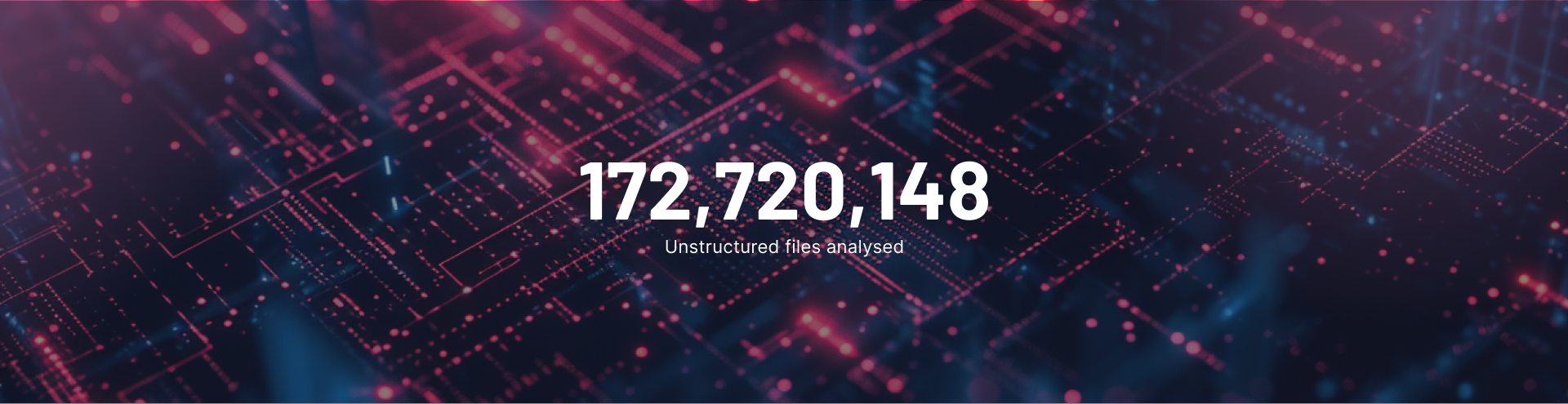
From insider errors to outsider leaks we detect:

Customer and employee PII

Financial documents and deal data

Source code and project files

Legal and compliance exposure

Credentials and keys
We work with security teams, incident response partners, and data leaders:

SOC teams seeking faster triage

CISOs dealing with board-level data risk

IR teams managing breach fallouts

Data stewards fixing what's broken before it leaks
Backed by information security leaders:




Let’s turn data disorder into strategic clarity.